Jarek Sygitowicz
Digital ID = fascist regime?
One of the most frequent criticisms of the government-issued eIDs is the privacy aspect. To be precise, the lack of privacy. Totalitarian control and surveillance of any action an eID user takes.

The protocol used to build EUDI (EU Digital Identity wallet) was designed to prevent such a situation. So let’s debunk the surveillance myth and learn a bit about the Verifiable Credentials protocol in the process.
How governments are issuing credentials (eID)
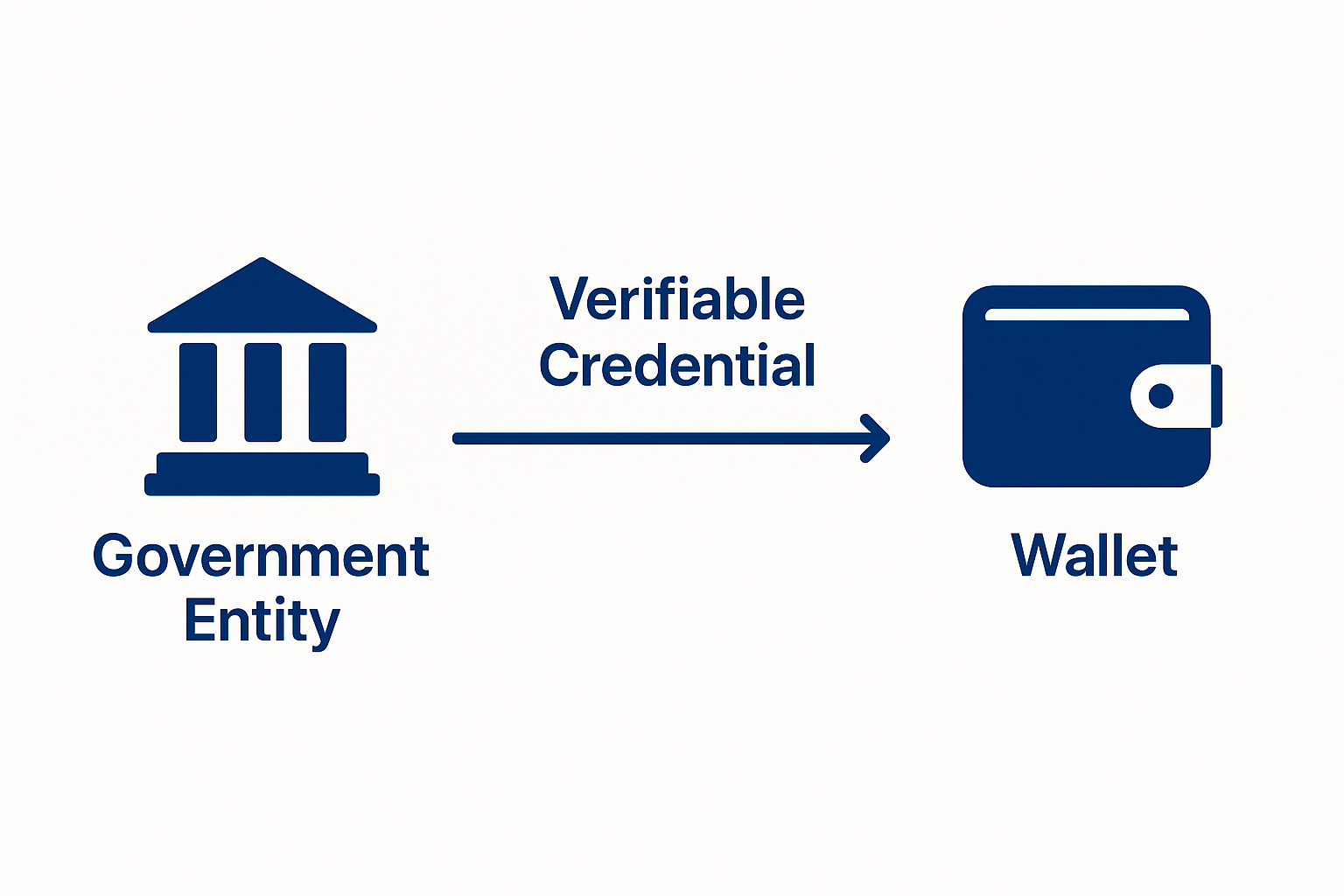
First of all, the Verifiable Credentials protocol mimics the physical world in the sense that eID issuance is similar to issuing a plastic document. Slightly oversymplified process looks like this: you go to the issuer's website, ask for a credential, and you receive it into your wallet.
From now on, the data sits on your phone, with a cryptographic signature proving that it was, in fact, issued by the government.
Cryptographic signature is the most important element of trust. You can be sure who the issuer is, but you can also be sure that the data in the wallet was not changed in any way.
How is your wallet protecting your privacy?
Let’s see what kind of tools, wallet can use to protect user’s privacy.
Selective disclosure
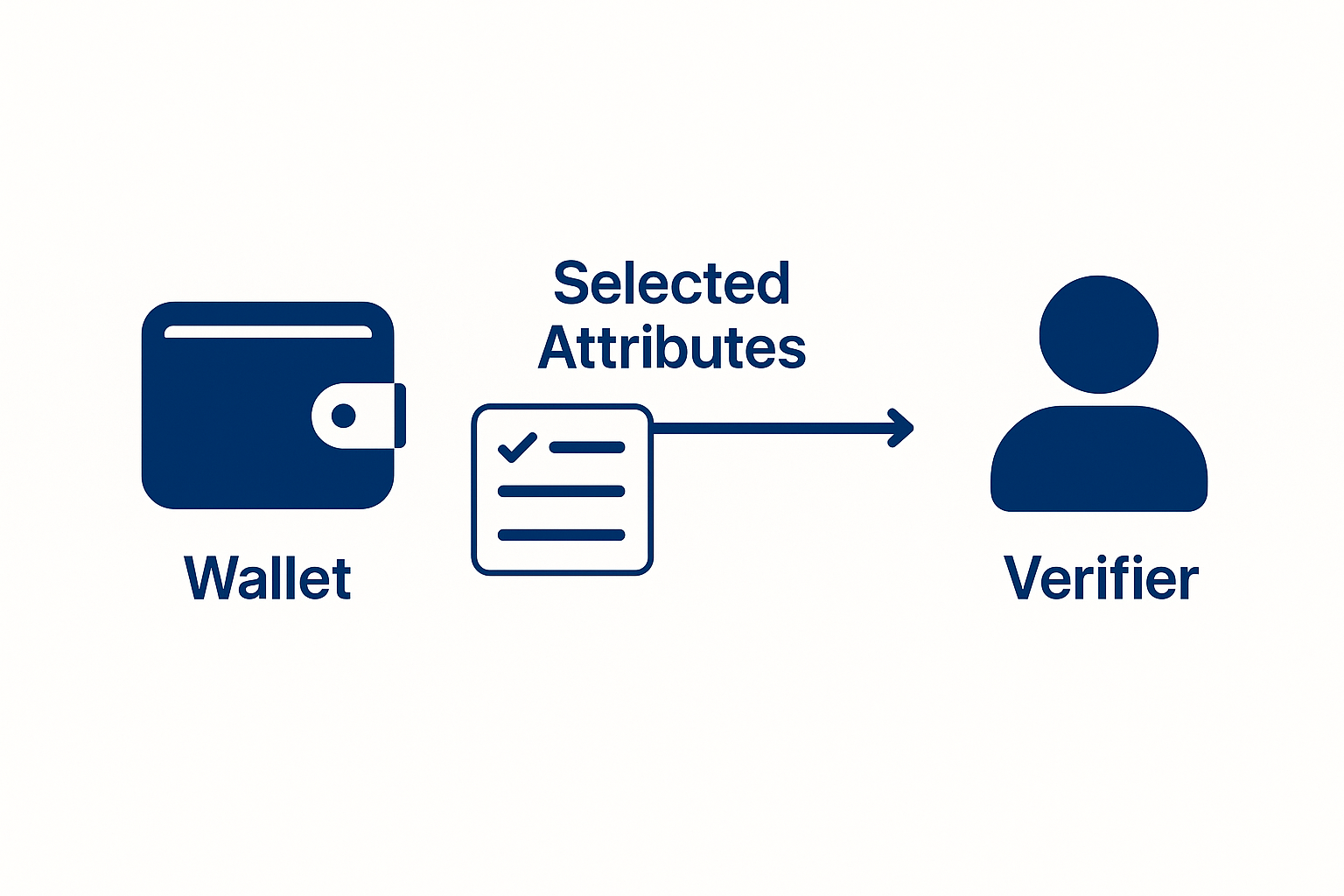
Unlike with the plastic document, where users are sending pictures of back and front of the documents, Verifiable Credentials can send only the information needed for the process.
If you need First Name and Last Name, you can only send this information and nothing else.
Zero-knowledge proofs
A more extreme version of selective disclosure is a zero-knowledge proof, where a website can check your age without knowing your exact birth date.
How does that work? The requesting website asks the wallet, “Are you over 18 years old?” and the wallet, based on the information it has, can respond “Yes” or “No”.
No other information is shared.
What does the government know about your activities?
The most important part, is that by definition credentials issuer has no idea where the wallet is sending those credentials.
Whole data exchange happens only between the wallet and the verifier.
But how does the verifier know, that the attributes (eID) being sent is really government-issued without contacting the government?
Well, this part is done via cryptographic signatures.
As mentioned before, issuing party signature not only guarantees immutability of information, it also confirms the source.
So, is the eID a totalitarian dream come true, that will allow governments to track everything we do? If it’s implemented using Verifiable Credentials it is not.
There is one caveat, though.
In the EUDI implementation, privacy and security are treated dead serious. All Relaying Parties (companies that can request data from the wallet) need to be registered, and each one will get approval for a specific set of data they can request within their license.
Those registries will be in every EU member state.
It depends on the wallet implementation, if the risk of leaking user activities via registry requests will be avoided. It’s all work in progress, so we can’t know for sure.
So is the eID (EUDI) ultimately tool for a totalitarian surveillance? Definitely not, but we need to pay close attention to the tiniest details of implementation.
Stay tuned for more updates!